new lcd panel ahs ability to record you in stock

Recordings include the active speaker and anything presented. You can also choose to record the meeting"s captions. Recordings are saved to the organizer’s Meet Recordings folder in My Drive. An email with the recording link is sent to the meeting organizer and the person who started the recording. The link is added to the Calendar event.
Tip: If you record captions, the recording file might be ready before the captions are available if played on Google Drive. The captions may become playable a few hours after the recording file is generated.
Important: Recording is only available from Meet on a computer. Mobile app users are notified when the recording starts or stops, but can"t control recording.
In some cases, the recording file might be ready before the captions are available if the recording is played on Google Drive. The captions may become playable a few hours after the recording file is generated.
The recording is saved to the meeting organizer’s My Drive > Meet Recordings folder. An email with the recording link is sent to the meeting organizer and the person who started the recording.
Recordings save to the meeting organizer’s My Drive > Meet Recordings folder. However, if the organizer changes or if the meeting occurs outside of the scheduled Calendar time, the recording link is sent to the original event creator.
If the recording starts at the scheduled meeting time, the recording links to the Google Calendar event. Individual meeting participants in the same organization as the meeting organizer automatically get access to the recording. Groups don"t automatically get access.
Important:Once you meet your storage quota, you get an alert on Meet. We recommend you keep track of your available storage space through Google Drive or Google storage page.

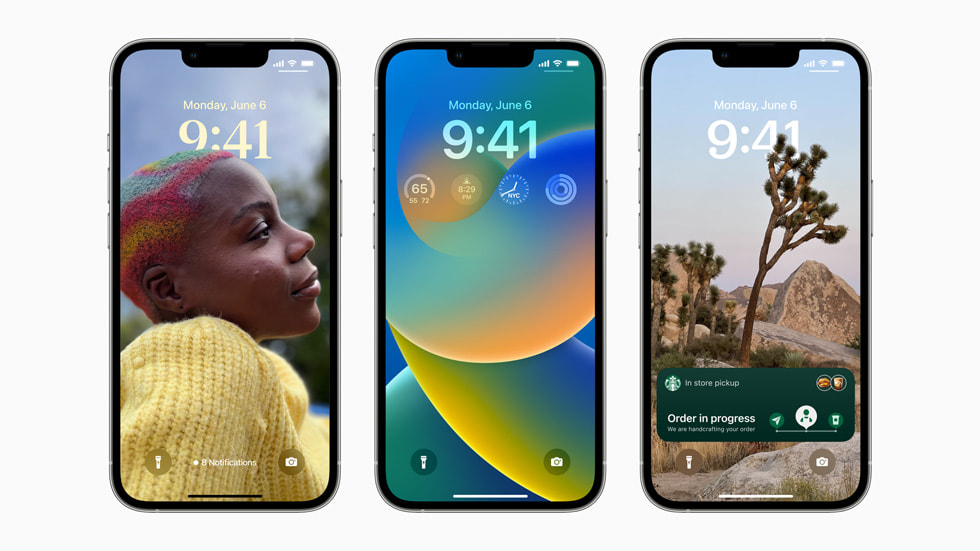
For inspiration on how to make the Lock Screen your own, browse a gallery of many options, each with a unique backdrop, stylized view of the date and time, and information you can see at a glance.
See a set of photos shuffle automatically on your Lock Screen. Set the cadence for how often your Lock Screen updates with a new photo, or let iOS surprise and delight you throughout the day.
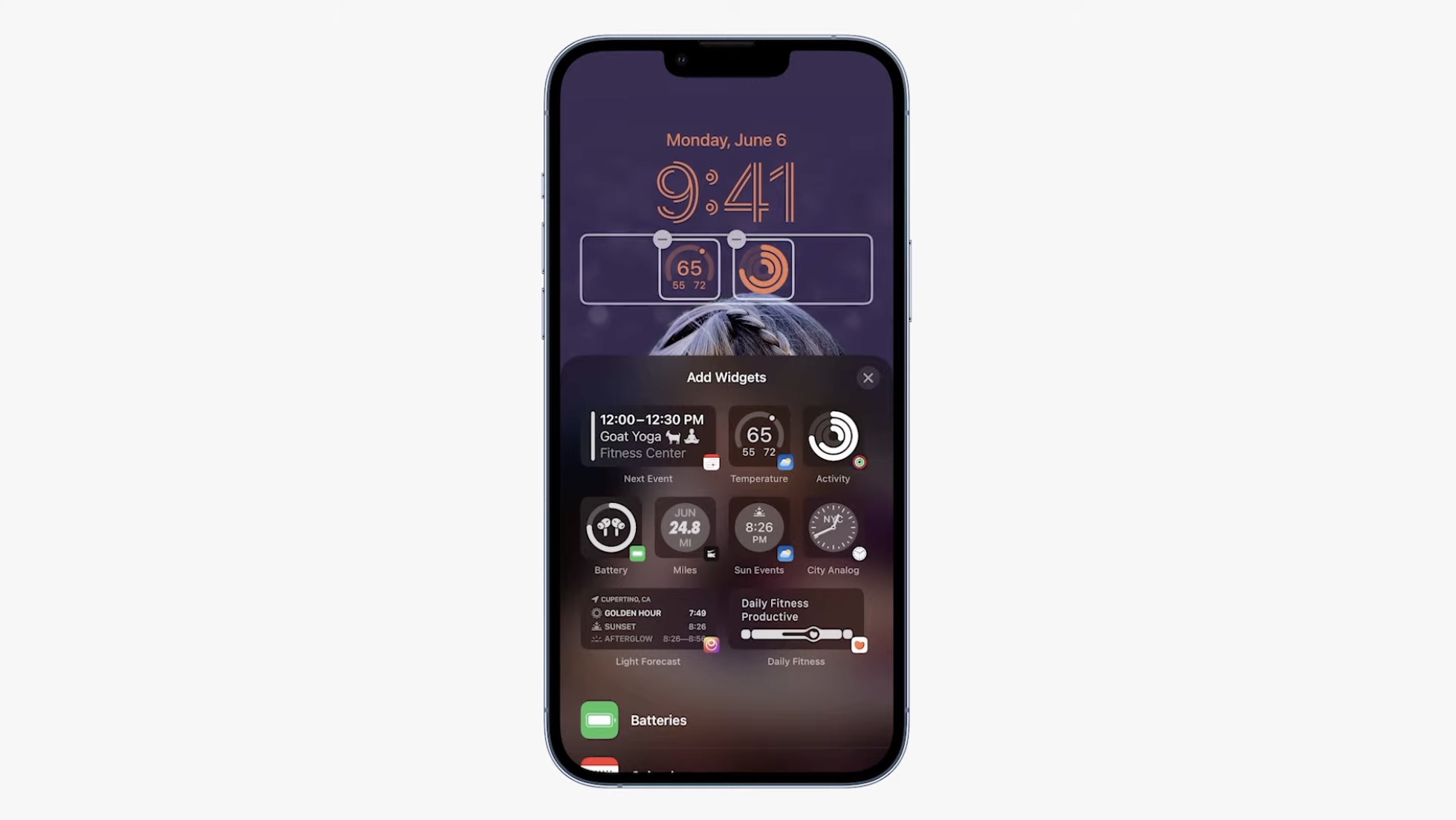
Choose to display a set of widgets as part of your Lock Screen to glance at information like the weather, time, date, battery levels, upcoming calendar events, alarms, time zones, and Activity ring progress.
Glance at widgets from your favorite third-party apps. View widgets in a textual, circular, or rectangular format near the time to get information like weather conditions or progress on your goals.
Follow an ongoing sports game or track the progress of your ride or order with just a glance. Glance at Live Activities from your favorite third-party apps with the new developer API.
iOS suggests a relevant set of Lock Screens for provided Focus options, such as a data-rich Lock Screen while you’re using the Work Focus or a photo Lock Screen while you’re using the Personal Focus.
Choose from a set of dynamic, classic, and landscape Lock Screens created especially for iOS 16. Apple collections include Lock Screens to celebrate special cultural moments, like Pride and Unity.
Notifications, including your notification summary, now roll in from the bottom of your Lock Screen, making them easy to see at a glance as they come in.
Transform how your iPhone looks and functions at the same time by connecting your Lock Screen to your Focus. To activate a Focus, you can swipe to the corresponding Lock Screen.
iOS suggests a relevant set of Lock Screens for provided Focus options, such as a data-rich Lock Screen while you’re using the Work Focus or a photo Lock Screen while you’re using the Personal Focus.
Set boundaries within Apple apps like Calendar, Mail, Messages, and Safari for each Focus you enable. For example, choose a set of Tab Groups to show up in Safari while in the Work Focus, or hide your work calendar when you’re using the Personal Focus.
Contribute photos manually, or use smart features to make sharing seamless, like a switch in Camera, automatic sharing using Bluetooth proximity, and sharing suggestions in For You.
Developers can build a Shared with You section into their app, so when someone sends you a video or article that you don’t have time to check out at the moment, it will be easy to find the next time you open the app.
Send an invitation to collaborate on a project in Messages, and everyone on the thread will automatically be added to the document, spreadsheet, or project. Compatible with Files, Keynote, Numbers, Pages, Notes, Reminders, and Safari, as well as third‑party apps.
Developers can integrate their app’s collaboration experiences with Messages and FaceTime, making it easy to initiate and manage collaboration from the places where you’re communicating with your collaborators.
See available extensions from your other devices listed in Safari preferences. Once installed, an extension will sync so you only have to turn it on once.
Sign in to websites or apps on other devices, including non‑Apple devices, with your saved passkey by scanning the QR code with your iPhone or iPad and using Face ID or Touch ID to authenticate.
Text is completely interactive in paused video frames, so you can use functions like copy and paste, lookup, and translate. Live Text works in Photos, Quick Look, Safari, and more.
Data detected in photos and videos is actionable with a single tap. Track flights or shipments, translate foreign languages, convert currencies, and more.
Discover Siri capabilities in iOS and apps by asking “Hey Siri, what can I do here?” You can also inquire about a specific app by saying, for example, “Hey Siri, what can I do with iRobot?”
Siri can help you to hang up a call completely hands free. Just say “Hey Siri, hang up” (participants on the call will hear you). You can enable this feature in Settings.
While dictating on device, you can move fluidly between voice and touch. Type with the keyboard, tap in the text field, move the cursor, and insert QuickType suggestions, all without needing to stop Dictation.
Share your ID information in apps that require identity and age verification. Apps will only request information needed to complete the transaction. You will be able to review this request, and your data will be shared only after authorizing with Face ID or Touch ID.
As part of Apple Card, the Daily Cash hub helps you learn how to earn Daily Cash, view the lifetime Daily Cash you’ve received, track your progress toward offers, and find the latest Bonus Daily Cash Merchants.
Customers in the U.S. will be able to share their verified information from their ID card in Wallet within apps that require age or identity verification.
You no longer need to add a new hotel key in Wallet for each new reservation: A single key allows you to check in and unlock your room for all your upcoming stays at hotels within the same brand.
Apple Pay Order Tracking allows users to receive detailed receipts and order tracking information in Wallet for Apple Pay purchases with participating merchants.
Now you can specify purchase amounts for multiple merchants within a single Apple Pay payment sheet. This gives you the flexibility to make a bundled purchase — such as a travel package with flight, rental car, and hotel — then send payments to individual merchants.
The Home app has an all‑new design that makes it easier to navigate, organize, view, and control all your accessories. Improvements to the underlying architecture enhance your smart home’s performance and make it more efficient and reliable.
See your entire home at a glance in the redesigned Home tab. Rooms and favorite accessories are integrated into the app’s main tab, giving you easier access to accessories you use most.
Categories for Lights, Climate, Security, Speakers and TVs, and Water let you quickly access all the relevant accessories organized by room, along with more detailed status information.
Accessory tiles have been redesigned so the different accessories are more visually recognizable through shape and color. Accessories can be controlled directly from their tiles by tapping the tile’s icon, or you can tap the accessory name for more detailed controls.
Enhancements to the underlying architecture enable faster, more reliable performance, especially for homes with many smart accessories. Communicate with and control connected accessories more efficiently from multiple devices at the same time using the Home app.
Matter is a new smart home connectivity standard that will enable compatible accessories to work together seamlessly, across platforms. Matter will allow you to choose from even more compatible smart home accessories and control them with the Home app and Siri on Apple devices.
You can quickly add your medications by using your iPhone camera. Simply position the medication label in the frame and you’ll see results for medication name, strength, and form.
Log when you’ve taken your medications from a reminder or log medications right in the Health app. Interactive charts help you understand when you’ve taken your medications and give you insight into your medication adherence.
Educational content on medications you’re taking gives you more context, including how to pronounce the name, what the medication is used for, how it works, and potential side effects.
Taking certain medications together can make them less effective or cause side effects. To help with this, when you add a new medication you’ll receive an alert if there is a critical interaction. You can review critical, serious, and moderate interactions in the Health app.
You can receive a notification if your logged menstrual cycles show a pattern of infrequent periods, irregular periods, prolonged periods, or persistent spotting.
Track and meet your fitness goals even if you don’t have an Apple Watch. Using iPhone motion sensors, your steps, distance, and third‑party workouts will give you an estimate of your calories to contribute to your daily Move goal.
Set up an account for a child with the right parental controls, right from the start, including easy‑to‑use, age-appropriate suggestions for media restrictions.
Family Checklist gives you helpful tips and suggestions like updating a child’s settings as they get older, turning on location sharing, or just reminding you that you can share your iCloud+ subscription with everyone.
The next generation of CarPlay covers all of a driver’s screens for a cohesive experience. Deep communication with the vehicle’s systems allows for driving information on instrument cluster displays and control of the radio and HVAC. This new version of CarPlay is specific to each vehicle, accommodating unique screen shapes and layouts. New levels of personalization allow drivers to choose their gauge cluster design, including brand‑specific options.
Fueling and driving task apps are available in CarPlay. Your favorite apps that help you fill your tank and provide you with road information, toll support, towing help, and more can find a home in CarPlay.
This new section in Settings helps people in domestic or intimate partner violence situations quickly reset the access they’ve granted to others. It also helps you manage which people and apps you’ve given access to.
Stream video directly from devices that support non‑AirPlay streaming protocols without having to provide Bluetooth or local network access permission.
The Hidden and Recently Deleted albums are locked by default and can be unlocked using your iPhone authentication method: Face ID, Touch ID, or your passcode.
This new security mode provides extreme protection for the very small number of users who face grave, targeted threats to their digital security. It further hardens your device’s defenses and strictly limits certain functions, sharply reducing the attack surface that could potentially be exploited by highly targeted mercenary spyware.
Fully control Apple Watch from iPhone and use Switch Control, Voice Control, or any other assistive features on iPhone to get the most out of your Apple Watch.
Siri can help you to hang up a call completely hands free. Just say “Hey Siri, hang up” (participants on the call will hear you). You can enable this feature in Settings.
You can now hang up Phone and FaceTime calls with Voice Control. Just use the voice command “hang up” when Voice Control is turned on (participants on the call will hear you).
Transcriptions are generated automatically in real time for users who are deaf or hard of hearing so they can follow along more easily with conversations, audio, and video.
See automatically transcribed dialogue integrated into your FaceTime video calls. With speaker attribution, it’s easy to follow along with group conversations.
VoiceOver and Spoken Content are now available in over 20 additional languages and locales, including Bangla (India), Bulgarian, Catalan, Ukrainian, and Vietnamese. You can also select from dozens of new voices optimized for assistive features.
Train iPhone to listen to sounds that are specific to your environment, such as the beeping sound of an electrical appliance in your kitchen, the precise ring of the doorbell in your home, and more.

UPDATE 1/26: We are beginning to roll out screen recording in Snipping Tool to Windows Insiders in the Beta Channel (version 11.2212.24.0). And as part of the most recent Snipping Tool update, we have also added the ability to pause while recording and you should notice improved performance and reliability.
Hello Windows Insiders, today we are beginning to roll out an update to the Snipping Tool app (version 11.2211.35.0) for Windows 11 to Windows Insiders in the Dev Channel. We are just beginning the roll out now so not all Insiders in the Dev Channel will receive the update right away.
We know that Snipping Tool is a favorite among the Insider community, so we are very excited to introduce a built-in screen recorder with this update! Snipping Tool has always made it quick and easy to capture and share content from your PC, and with screen recording built-in, we are expanding these capabilities to even more types of content.
You will then be able to select and refine the part of your screen that you want to record before starting your screen recording session. When you are finished, you can preview your recording before saving or sharing it with others.
We are aware of a couple issues that may impact your experience with this preview. Some users might notice a slight delay between when you click “Start” and when the recording begins. There is also a known issue where the Snipping Tool app window does not restore when initiating a new snip from within the app.
After adding the shortcut, you begin by opening Control Center. On iPhones older than the iPhone X, get there by swiping up from the bottom of the screen. On newer iPhones, swipe down from the top-right corner of the screen.
Tap on the Screen Recording button, which will prompt a countdown inside the button followed by it turning red to indicate to begin capturing whatever"s on your display.
What if you want to walk someone through how to use a feature or get past a bug you keep running into? Well, you can turn on your phone"s microphone and have it record for as long as a screen-recording session is active.
Once you stop recording, you"ll be asked if you want to save the video to the Photos app. Open the Photos app to view, edit, crop, and share the video through Messages, email, or even post it to your favorite social network.
In Microsoft Teams, users can record their Teams meetings and group calls to capture audio, video, and screen sharing activity. There is also an option for recordings to have automatic transcription, so that users can play back meeting recordings with closed captions and review important discussion items in the transcript. The recording happens in the cloud and is saved to OneDrive and SharePoint, so users can share it securely across their organization.
The change from using Microsoft Stream (classic) to OneDrive and SharePoint for meeting recordings will automatically happen in August 2021. For detailed information, see Use OneDrive and SharePoint or Stream for meeting recordings.
For information about using roles in Teams meetings, and how to change users" roles, see Roles in a Teams meeting. For live events recording options, see Live event recording policies in Teams.
For a Teams user"s meetings to be recorded, OneDrive and SharePoint must be enabled for the tenant. In addition, the following prerequisites are required for both the meeting organizer and the person who is initiating the recording:
To enable channel meeting recordings to be saved so channel members can"t edit or download the recordings the CSTeamsMeetingPolicy -ChannelRecordingDownload setting must be set to Block.
Users won"t need OneDrive or SharePoint enabled if you want users to only record and download the recordings. This will mean that the recordings aren"t stored in OneDrive or SharePoint, but are instead stored in temporary Teams storage with a 21-day limit before it"s deleted. It"s not something that an admin can control, manage, or delete at this time.
In the Microsoft Teams admin center, turn on or turn off the Meeting recording setting in the meeting policy. To learn more, see Meeting policy settings for audio and video.
Using PowerShell, you configure the AllowCloudRecording setting in TeamsMeetingPolicy. To learn more, see New-CsTeamsMeetingPolicy and Set-CsTeamsMeetingPolicy.
Both the meeting organizer and the recording initiator need to have the recording permissions to record the meeting. Unless you have assigned a custom policy to the users, users get the Global policy, which has AllowCloudRecording enabled by default.
If a Teams user from an external tenant that is enabled for Teams policy-based compliance recording joins a meeting or call on your tenant, that meeting/call will be recorded by the other tenant for compliance purposes regardless of cloud based recording turned on or off on your tenant. Presenters that are part of the meeting in your tenant are advised to remove the user from the meeting if recordings should not be captured by users from another tenant. For more information about policy based compliance recording on Teams, see Introduction to Teams policy-based recording for calling & meetings.
This setting controls if channel meetings are saved to a "Recordings" folder or a "Recordings\View only" folder in the channel. The setting applies to the policy of the user who selects record for the channel meeting.
Allow (default)—Saves channel meeting recordings to a "Recordings" folder in the channel. The permissions on the recording files will be based off the Channel SharePoint permissions. This is the same as any other file uploaded for the channel.
Block—Saves channel meeting recordings to a "Recordings\View only" folder in the channel. Channel owners will have full rights on the recordings in this folder, but channel members will have read access without ability to download.
Using PowerShell, you configure the ChannelRecordingDownload setting in TeamsMeetingPolicy. To learn more, see New-CsTeamsMeetingPolicy and Set-CsTeamsMeetingPolicy.
The ChannelRecordingDownload setting is only available in the Teams PowerShell module version 2.4.1-preview or higher. To download the latest preview version of the module use this command:
This setting controls whether captions and transcription features are available during playback of meeting recordings. The person who started the recording needs this setting turned on for these features to work with their recording.
Turning this setting on creates a copy of the transcript that is stored with the meeting recording which enables Search, CC, and transcripts on the meeting recording.
That transcription for recorded meetings is currently only supported for English (US), English (Canada), English (India), English (UK), English (Australia), English (New Zealand), Arabic (United Arab Emirates) , Arabic (Saudi Arabia) , Chinese (Simplified, China), Chinese (Traditional, Hong Kong SAR), Chinese (Traditional, Taiwan), Czech (Czechia) , Danish (Denmark), Dutch (Belgium) , Dutch (Netherlands), French (Canada), French (France), Finnish (Finland) , German (Germany), Greek (Greece), Hebrew (Israel) , Hindi (India), Hungarian (Hungary), Italian (Italy), Japanese (Japan), Korean (Korea) , Norwegian (Norway), Polish (Poland) , Portuguese (Brazil), Portuguese (Portugal), Romanian (Romania), Russian (Russia), Slovak (Slovakia), Spanish (Mexico), Spanish (Spain), Swedish (Sweden), Thai (Thailand) , Turkish (Turkey), Ukrainian (Ukraine), Vietnamese (Vietnam). They are stored together with the meeting recordings in OneDrive and SharePoint cloud storage.
You can use the Microsoft Teams admin center or PowerShell to set a Teams meeting policy to control whether the recording initiator gets a choice to transcribe the meeting recording.
In the Microsoft Teams admin center, turn on or turn off the Allow transcription setting in the meeting policy. To learn more, see Meeting policy settings for audio and video.
Using PowerShell, you configure the AllowTranscription setting in TeamsMeetingPolicy. To learn more, see New-CsTeamsMeetingPolicy and Set-CsTeamsMeetingPolicy.
If your organization has a meeting recording policy that you would like your users to accept before recording a meeting, use the Azure Active Directory terms of use feature. This feature allows your users to accept your organization"s terms of user policy before getting access to Microsoft Teams. This feature is not specific to clicking the record button, but is related to using Teams or other Microsoft 365 apps overall. Our suggestion is to add your meeting recording information to your overall terms of use for using Teams or Microsoft 365.
As an admin, you can update the Teams recording and transcription privacy policy URL with a custom link for your organization. You can do this in the Azure AD admin center using the following steps:
After adding your privacy policy URL, the default Teams meeting recording and transcription privacy statement will be replaced with the new URL provided by your organization.
Anonymous, guest, and federated users who join Teams meetings hosted by your organization will still have the default Teams meeting recording and transcription privacy policy.
Meeting recordings are stored in OneDrive and SharePoint cloud storage. The location and permissions depend on the type of meeting and the role of the user in the meeting. The default permissions applied to the recording are listed below, users that have full edit rights on the video recording file can change the permissions and share it later with others as needed.
People invited to the meeting, except external participants, will automatically be granted permission to the recording file with view access without ability to download.
If Set-CsTeamsMeetingPolicy -ChannelRecordingDownload is set to Allow (default) the member who clicked on Record has edit rights to the recording. Every other member’s permissions are based on the Channel SharePoint permissions.
If Set-CsTeamsMeetingPolicy -ChannelRecordingDownload is set to Block channel owners will have full rights on the recording, but channel members will have read access without ability to download.
If a meeting recording isn"t able to be uploaded to OneDrive and SharePoint, it will temporarily be available for download from Teams for 21 days before it is deleted. This is not something at this point that an admin can control or manage to include the ability to delete it.
The recording retention for this is temporary storage is affected by the chat message itself. As such, any deletion of the original chat message for the recording will prevent users from being able to access the recording. There are two scenarios that can affect this:
User manually deletes the chat message—In this scenario, as the original message is gone, users will no longer be able to access the recording and no further downloads will be possible. However, the recording itself may still be retained within Microsoft"s internal systems for a time (not exceeding the original 21-day period).
Recording chat message is deleted by chat retention policy—Temporary storage recordings are directly tied to the chat retention policy. As such, although recordings on Teams temporary storage will by default be retained for 21 days before being deleted, if the chat message is deleted before the 21-day time period, due to chat message retention policies, the recording will also be deleted. There is no way to recover the recording after this.
The size of a 1-hour recording is 400 MB. Make sure you understand the capacity required for recorded files and have sufficient storage available in OneDrive and SharePoint. Read Set the default storage space for OneDrive and Manage SharePoint site storage limits to understand the base storage included in the subscription and how to purchase additional storage.
Meeting recordings are stored as video files in OneDrive and SharePoint and follow management and governance options available in those platforms. Read SharePoint governance overview for more information.
For non-channel meetings, the recordings are stored in the recorder"s OneDrive, thus handling ownership and retention after an employee leaves will follow the normal OneDrive and SharePoint process.
Meeting recordings have a Default expiration time of 120 days. You can turn off the Recordings automatically expire setting or change the Default expiration time. Learn more about meeting recordings automatically expiring.
Closed captions for Teams meeting recordings will be available during playback only if the user had transcription turned on at the time of recording. Admins must turn on recording transcription via policy to ensure their users have the option to record meetings with transcription.
Captions help create inclusive content for viewers of all abilities. As an owner, you can hide captions on the meeting recording, although the meeting transcript will still be available on Teams unless you delete it there.
Today closed captions for the recording video file are linked to the Teams meeting transcript. This link will remain for the lifetime of the file in most cases, but can be broken if the video file is copied within the same OneDrive or SharePoint site, which would result in captions not being available on the copied video file.
Any future changes to the link between the transcript in Teams and the recording will be clarified here and in message center notifications. If we make any changes in the future, we will ensure recording files less than 60-days old display the transcript from the meeting as captions.
The meeting recordings are stored in OneDrive and SharePoint, which is Microsoft 365 and Office 365 Tier-D compliant. To support e-Discovery requests for compliance admins who are interested in meeting or call recordings, the recording completed message is available in the compliance content search functionality for Microsoft Teams. Compliance admins can look for the keyword "recording" in the subject line of the item in compliance content search preview and discover meeting and call recordings in the organization.
You can apply automatic retention labels to target just Teams meeting recording video files via the ProgID property. For more information, see How to auto-apply a retention label for Teams meeting recordings.
You can apply DLP policies to meeting recording files also by the ProgID property. In the DLP rule for files in SharePoint and OneDrive set the conditions to be:
The tests will return the best next steps to address any tenant or policy configurations to validate that the user is properly configured to record a meeting in Teams.
If you"re an administrator, you can use the following diagnostic tool to validate that the meeting recording completed successfully and it was uploaded to Stream or OneDrive, based on the meeting ID and recording start time:
In the Run diagnostic pane, enter the URL of the meeting in the URL of the meeting that was recorded field (usually found in the meeting invitation) as well as the date of the meeting in the When was the meeting recorded? field and then select Run Tests.
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
:max_bytes(150000):strip_icc()/how-to-screen-record-on-the-iphone-12-50846251-3ee09bd0b7244b3ca7fa03984f483a50.jpg)
Most companies keep sensitive personal information in their files—names, Social Security numbers, credit card, or other account data—that identifies customers or employees.
This information often is necessary to fill orders, meet payroll, or perform other necessary business functions. However, if sensitive data falls into the wrong hands, it can lead to fraud, identity theft, or similar harms. Given the cost of a security breach—losing your customers’ trust and perhaps even defending yourself against a lawsuit—safeguarding personal information is just plain good business.
Some businesses may have the expertise in-house to implement an appropriate plan. Others may find it helpful to hire a contractor. Regardless of the size—or nature—of your business, the principles in this brochure will go a long way toward helping you keep data secure.
Inventory all computers, laptops, mobile devices, flash drives, disks, home computers, digital copiers, and other equipment to find out where your company stores sensitive data. Also, inventory the information you have by type and location. Your file cabinets and computer systems are a start, but remember: your business receives personal information in a number of ways—through websites, from contractors, from call centers, and the like. What about information saved on laptops, employees’ home computers, flash drives, digital copiers, and mobile devices? No inventory is complete until you check everywhere sensitive data might be stored.
Track personal information through your business by talking with your sales department, information technology staff, human resources office, accounting personnel, and outside service providers. Get a complete picture of:Who sends sensitive personal information to your business. Do you get it from customers? Credit card companies? Banks or other financial institutions? Credit bureaus? Job applicants? Other businesses?
How your business receives personal information. Does it come to your business through a website? By email? Through the mail? Is it transmitted through cash registers in stores?
What kind of information you collect at each entry point. Do you get credit card information online? Does your accounting department keep information about customers’ checking accounts?
Where you keep the information you collect at each entry point. Is it in a central computer database? On individual laptops? On a cloud computing service? On employees’ smartphones, tablets, or other mobile devices? On disks or tapes? In file cabinets? In branch offices? Do employees have files at home?
Who has—or could have—access to the information. Which of your employees has permission to access the information? Do they need access? Could anyone else get a hold of it? What about vendors who supply and update software you use to process credit card transactions? Contractors operating your call center?Different types of information present varying risks. Pay particular attention to how you keep personally identifying information: Social Security numbers, credit card or financial information, and other sensitive data. That’s what thieves use most often to commit fraud or identity theft.
Yes. While you’re taking stock of the data in your files, take stock of the law, too. Statutes like the Gramm-Leach-Bliley Act, the Fair Credit Reporting Act, and the Federal Trade Commission Act may require you to provide reasonable security for sensitive information.
Effective data security starts with assessing what information you have and identifying who has access to it. Understanding how personal information moves into, through, and out of your business and who has—or could have—access to it is essential to assessing security vulnerabilities. You can determine the best ways to secure the information only after you’ve traced how it flows.
If you don’t have a legitimate business need for sensitive personally identifying information, don’t keep it. In fact, don’t even collect it. If you have a legitimate business need for the information, keep it only as long as it’s necessary.
Use Social Security numbers only for required and lawful purposes— like reporting employee taxes. Don’t use Social Security numbers unnecessarily—for example, as an employee or customer identification number, or because you’ve always done it.
If your company develops a mobile app, make sure the app accesses only data and functionality that it needs. And don’t collect and retain personal information unless it’s integral to your product or service. Remember, if you collect and retain data, you must protect it.
Don’t keep customer credit card information unless you have a business need for it. For example, don’t retain the account number and expiration date unless you have an essential business need to do so. Keeping this information—or keeping it longer than necessary—raises the risk that the information could be used to commit fraud or identity theft.
Scale down access to data. Follow the “principle of least privilege.” That means each employee should have access only to those resources needed to do their particular job.
We like to have accurate information about our customers, so we usually create a permanent file about all aspects of their transactions, including the information we collect from the magnetic stripe on their credit cards. Could this put their information at risk?
Yes. Keep sensitive data in your system only as long as you have a business reason to have it. Once that business need is over, properly dispose of it. If it’s not in your system, it can’t be stolen by hackers.
If you must keep information for business reasons or to comply with the law, develop a written records retention policy to identify what information must be kept, how to secure it, how long to keep it, and how to dispose of it securely when you no longer need it.
What’s the best way to protect the sensitive personally identifying information you need to keep? It depends on the kind of information and how it’s stored. The most effective data security plans deal with four key elements: physical security, electronic security, employee training, and the security practices of contractors and service providers.
Many data compromises happen the old-fashioned way—through lost or stolen paper documents. Often, the best defense is a locked door or an alert employee.
Store paper documents or files, as well as thumb drives and backups containing personally identifiable information in a locked room or in a locked file cabinet. Limit access to employees with a legitimate business need. Control who has a key, and the number of keys.
Require that files containing personally identifiable information be kept in locked file cabinets except when an employee is working on the file. Remind employees not to leave sensitive papers out on their desks when they are away from their workstations.
If you maintain offsite storage facilities, limit employee access to those with a legitimate business need. Know if and when someone accesses the storage site.
If you ship sensitive information using outside carriers or contractors, encrypt the information and keep an inventory of the information being shipped. Also use an overnight shipping service that will allow you to track the delivery of your information.
If you have devices that collect sensitive information, like PIN pads, secure them so that identity thieves can’t tamper with them. Also, inventory those items to ensure that they have not been switched.
Computer security isn’t just the realm of your IT staff. Make it your business to understand the vulnerabilities of your computer system, and follow the advice of experts in the field.
Identify all connections to the computers where you store sensitive information. These may include the internet, electronic cash registers, computers at your branch offices, computers used by service providers to support your network, digital copiers, and wireless devices like smartphones, tablets, or inventory scanners.
Assess the vulnerability of each connection to commonly known or reasonably foreseeable attacks. Depending on your circumstances, appropriate assessments may range from having a knowledgeable employee run off-the-shelf security software to having an independent professional conduct a full-scale security audit.
Encrypt sensitive information that you send to third parties over public networks (like the internet), and encrypt sensitive information that is stored on your computer network, laptops, or portable storage devices used by your employees. Consider also encrypting email transmissions within your business.
Check expert websites (such as www.us-cert.gov) and your software vendors’ websites regularly for alerts about new vulnerabilities, and implement policies for installing vendor-approved patches to correct problems.
Restrict employees’ ability to download unauthorized software. Software downloaded to devices that connect to your network (computers, smartphones, and tablets) could be used to distribute malware.
don’t need, disable them to prevent hacks or other potential security problems. For example, if email service or an internet connection is not necessary on a certain computer, consider closing the ports to those services on that computer to prevent unauthorized access to that machine.
When you receive or transmit credit card information or other sensitive financial data, use Transport Layer Security (TLS) encryption or another secure connection that protects the information in transit.
Pay particular attention to the security of your web applications—the software used to give information to visitors to your website and to retrieve information from them. Web applications may be particularly vulnerable to a variety of hack attacks. In one variation called an “injection attack,” a hacker inserts malicious commands into what looks like a legitimate request for information. Once in your system, hackers transfer sensitive information from your network to their computers. Relatively simple defenses against these attacks are available from a variety of sources.
Yes. Regular email is not a secure method for sending sensitive data. The better practice is to encrypt any transmission that contains information that could be used by fraudsters or identity thieves.
Control access to sensitive information by requiring that employees use “strong” passwords. Tech security experts say the longer the password, the better. Because simple passwords—like common dictionary words—can be guessed easily, insist that employees choose passwords with a mix of letters, numbers, and characters. Require an employee’s user name and password to be different. Require password changes when appropriate, for example following a breach.
Warn employees about possible calls from identity thieves attempting to deceive them into giving out their passwords by impersonating members of your IT staff. Let employees know that calls like this are always fraudulent, and that no one should be asking them to reveal their passwords.
Caution employees against transmitting sensitive personally identifying data—Social Security numbers, passwords, account information—via email. Unencrypted email is not a secure way to transmit information.
Assess whether sensitive information really needs to be stored on a laptop. If not, delete it with a “wiping” program that overwrites data on the laptop. Deleting files using standard keyboard commands isn’t sufficient because data may remain on the laptop’s hard drive. Wiping programs are available at most office supply stores.
Require employees to store laptops in a secure place. Even when laptops are in use, consider using cords and locks to secure laptops to employees’ desks.
Consider allowing laptop users only to access sensitive information, but not to store the information on their laptops. Under this approach, the information is stored on a secure central computer and the laptops function as terminals that display information from the central computer, but do not store it. The information could be further protected by requiring the use of a token, “smart card,” thumb print, or other biometric—as well as a password—to access the central computer.
If a laptop contains sensitive data, encrypt it and configure it so users can’t download any software or change the security settings without approval from your IT specialists. Consider adding an “auto-destroy” function so that data on a computer that is reported stolen will be destroyed when the thief uses it to try to get on the internet.
Train employees to be mindful of security when they’re on the road. They should never leave a laptop visible in a car, at a hotel luggage stand, or packed in checked luggage unless directed to by airport security. If someone must leave a laptop in a car, it should be locked in a trunk. Everyone who goes through airport security should keep an eye on their laptop as it goes on the belt.
Our account staff needs access to our database of customer financial information. To make it easier to remember, we just use our company name as the password. Could that create a security problem?
Yes. Hackers will first try words like “password,” your company name, the software’s default password, and other easy-to-guess choices. They’ll also use programs that run through common English words and dates. To make it harder for them to crack your system, select strong passwords—the longer, the better—that use a combination of letters, symbols, and numbers. Don’t store passwords in clear text. Use a password management system that adds salt – random data – to hashed passwords and consider using slow hash functions.
Use a firewall to protect your computer from hacker attacks while it is connected to a network, especially the internet. A firewall is software or hardware designed to block hackers from accessing your computer. A properly configured firewall makes it tougher for hackers to locate your computer and get into your programs and files.
Determine whether you should install a “border” firewall where your network connects to the internet. A border firewall separates your network from the internet and may prevent an attacker from gaining access to a computer on the network where you store sensitive information. Set “access controls”—settings that determine which devices and traffic get through the firewall—to allow only trusted devices with a legitimate business need to access the network. Since the protection a firewall provides is only as effective as its access controls, review them periodically.
If some computers on your network store sensitive information while others do not, consider using additional firewalls to protect the computers with sensitive information.
Determine if you use wireless devices like smartphones, tablets, or inventory scanners or cell phones to connect to your computer network or to transmit sensitive information.
If you do, consider limiting who can use a wireless connection to access your computer network. You can make it harder for an intruder to access the network by limiting the wireless devices that can connect to your network.
Encrypt the information you send over your wireless network, so that nearby attackers can’t eavesdrop on these communications. Look for a wireless router that has Wi-Fi Protected Access 2 (WPA2) capability and devices that support WPA2.
Use encryption if you allow remote access to your computer network by employees or by service providers, such as companies that troubleshoot and update software you use to process credit card purchases. Consider implementing multi-factor authentication for access to your network.
Your information security plan should cover the digital copiers your company uses. The hard drive in a digital copier stores data about the documents it copies, prints, scans, faxes, or emails. If you don’t take steps to protect that data, it can be stolen from the hard drive, either by remote access or by extraction once the drive has been removed.
Get your IT staff involved when you’re thinking about getting a copier. Employees responsible for securing your computers also should be responsible for securing data on digital copiers.
When you’re buying or leasing a copier, consider data security features offered, either as standard equipment or as optional add-on kits. Typically, these features involve encryption and overwriting. Encryption scrambles the data on the hard drive so it can be read only by particular software. Overwriting—also known as file wiping or shredding—replaces the existing data with random characters, making it harder for someone to reconstruct a file.
Once you choose a copier, take advantage of all its security features. You may be able to set the number of times data is overwritten—generally, the more times the data is overwritten, the safer it is from being retrieved. In addition, make it an office practice to securely overwrite the entire hard drive at least once a month.
When you return or dispose of a copier, find out whether you can have the hard drive removed and destroyed, or overwrite the data on the hard drive. Have a skilled technician remove the hard drive to avoid the risk of breaking the machine.
To detect network breaches when they occur, consider using an intrusion detection system. To be effective, it must be updated frequently to address new types of hacking.
Maintain central log files of security-related information to monitor activity on your network so that you can spot and respond to attacks. If there is an attack on your network, the log will provide information that can identify the computers that have been compromised.
Monitor incoming traffic for signs that someone is trying to hack in. Keep an eye out for activity from new users, multiple log-in attempts from unknown users or computers, and higher-than-average traffic at unusual times of the day.
Monitor outgoing traffic for signs of a data breach. Watch for unexpectedly large amounts of data being transmitted from your system to an unknown user. If large amounts of information are being transmitted from your network, investigate to make sure the transmission is authorized.
Yes. There are simple fixes to protect your computers from some of the most common vulnerabilities. For example, a threat called an “SQL injection attack” can give fraudsters access to sensitive data on your system.
Protect your systems by keeping software updated and conducting periodic security reviews for your network. Bookmark the websites of groups like the Open Web Application Security Project, www.owasp.org, or SANS (SysAdmin, Audit, Network, Security) Institute’s The Top Cyber Security Risks, www.sans.org/top20, for up-to-date information on the latest threats—and fixes. And check with your software vendors for patches that address new vulnerabilities. For more tips on keeping sensitive data secure, read Start with Security: A Guide for Business.
Your data security plan may look great on paper, but it’s only as strong as the employees who implement it. Take time to explain the rules to your staff, and train them to spot security vulnerabilities. Periodic training emphasizes the importance you place on meaningful data security practices. A well-trained workforce is the best defense against identity theft and data breaches.
Ask every new employee to sign an agreement to follow your company’s confidentiality and security standards for handling sensitive data. Make sure they understand that abiding by your company’s data security plan is an essential part of their duties. Regularly remind employees of your company’s policy—and any legal requirement—to keep customer information secure and confidential.
Know which employees have access to consumers’ sensitive personally identifying information. Pay particular attention to data like Social Security numbers and account numbers. Limit access to personal information to employees with a “need to know.”
Have a procedure in place for making sure that workers who leave your employ or transfer to another part of the company no longer have access to sensitive information. Terminate their passwords, and collect keys and identification cards as part of the check-out routine.
Create a “culture of security” by implementing a regular schedule of employee training. Update employees as you find out about new risks and vulnerabilities. Make sure training includes employees at satellite offices, temporary help, and seasonal workers. If employees don’t attend, consider blocking their access to the network.
Train employees to recognize security threats. Tell them how to report suspicious activity and publicly reward employees who alert you to vulnerabilities. Visit ftc.gov/startwithsecurity to show them videos on vulnerabilities that could affect your company, along with practical guidance on how to reduce data security risks.Tell employees about your company policies regarding keeping information secure and confidential. Post reminders in areas where sensitive information is used or stored, as well as where employees congregate. Make sure your policies cover employees who telecommute or access sensitive data from home or an offsite location.
Teach employees about the dangers of spear phishing—emails containing information that makes the emails look legitimate. These emails may appear to come from someone within your company, generally someone in a position of authority. Make it office policy to independently verify any emails requesting sensitive information. When verifying, do not reply to the email and do not use links, phone numbers, or websites contained in the email.
Warn employees about phone phishing. Train them to be suspicious of unknown callers claiming to need account numbers to process an order or asking for customer or employee contact information. Make it office policy to double-check by contacting the company using a phone number you know is genuine.
Before you outsource any of your business functions— payroll, web hosting, customer call center operations, data processing, or the like—investigate the company’s data security practices and compare their standards to yours. If possible, visit their facilities.
Insist that your service providers notify you of any security incidents they experience, even if the incidents may not have led to an actual compromise of your data.
What looks like a sack of trash to you can be a gold mine for an identity thief. Leaving credit card receipts or papers or CDs with personally identifying information in a dumpster facilitates fraud and exposes consumers to the risk of identity theft. By properly disposing of sensitive information, you ensure that it cannot be read or reconstructed.
Implement information disposal practices that are reasonable and appropriate to prevent unauthorized access to—or use of—personally identifying information. Reasonable measures for your operation are based on the sensitivity of the information, the costs and benefits of different disposal methods, and changes in technology.
Effectively dispose of paper records by shredding, burning, or pulverizing them before discarding. Make shredders available throughout the workplace, including next to the photocopier.
When disposing of old computers and portable storage devices, use software for securely erasing data, usually called wipe utility programs. They’re inexpensive and can provide better results by overwriting the entire hard drive so that the files are no longer recoverable. Deleting files using the keyboard or mouse commands usually isn’t sufficient because the files may continue to exist on the computer’s hard drive and could be retrieved easily.
Make sure employees who work from home follow the same procedures for disposing of sensitive documents and old computers and portable storage devices.
If you use consumer credit reports for a business purpose, you may be subject to the FTC’s Disposal Rule. For more information, see Disposing of Consumer Report Information? Rule Tells How.
My company collects credit applications from customers. The form requires them to give us lots of financial information. Once we’re finished with the applications, we’re careful to throw them away. Is that sufficient?
No. Have a policy in place to ensure that sensitive paperwork is unreadable before you throw it away. Burn it, shred it, or pulverize it to make sure identity thieves can’t steal it from your trash.
Taking steps to protect data in your possession can go a long way toward preventing a security breach. Nevertheless, breaches can happen. Here’s how you can reduce the impact on your business, your employees, and your customers:
Consider whom to notify in the event of an incident, both inside and outside your organization. You may need to notify consumers, law enforcement, customers, credit bureaus, and other businesses that may be affected by the breach. In addition, many states and the federal bank regulatory agencies have laws or guidelines addressing data breaches. Consult your attorney.
No. There’s no one-size-fits-all approach to data security, and what’s right for you depends on the nature of your business and the kind of information you collect from your customers. Some of the most effective security measures—using strong passwords, locking up sensitive paperwork, training your staff, etc.—will cost you next to nothing and you’ll find free or low-cost security tools at non-profit websites dedicated to data security. Furthermore, it’s cheaper in the long run to invest in better data security than to lose the goodwill of your customers, defend yourself in legal actions, and face other possible consequences of a data breach.
The FTC works to prevent fraudulent, deceptive and unfair business practices in the marketplace and to provide information to help consumers spot, stop and avoid them. To file a complaint or get free information on consumer issues, visit ftc.gov or call toll-free, 1-877-FTC-HELP (1-877-382-4357); TTY: 1-866-653-4261.
Watch a video, How to File a Complaint, at ftc.gov/video to learn more. The FTC enters consumer complaints into the Consumer Sentinel Network, a secure online database and investigative tool used by hundreds of civil and criminal law enforcement agencies in the U.S. and abroad.
The National Small Business Ombudsman and 10 Regional Fairness Boards collect comments from small businesses about federal compliance and enforcement activities. Each year, the Ombudsman evaluates the conduct of these activities and rates each agency’s responsiveness to small businesses. Small businesses can comment to the Ombudsman without fear of reprisal. To comment, call toll-free 1-888-REGFAIR (1-888-734-3247) or go to www.sba.gov/ombudsman.
Easily share your creations in multiple channels. Let more viewers watch, pause and rewind on their schedule while maximizing time by eliminating unnecessary meetings.Learn more
Collect video assignments to ensure any team or student is heard. Track viewing activity and add interactive questions and more to ensure your message is understood.Learn more

If you"re using Skype for Mac on macOS 10.15 (Catalina), Skype requires access to Screen recording in the Mac System Preferences to share your screen during a call. You will either get a Skype notification directing you to Settings, or you will need to grant Skype access for Screen Recording in macOS Catalina System Preferences. Please go to Mac System Preferences > Security & Privacy > Screen Recording, and grant access to Skype.
Screen sharing is supported on Android 6.0 and above. For iPhone, iPad and iPod Touch with iOS 12 and above, this is supported on iPhone 6s, iPad Air 2, iPad mini 2019, iPod Touch 7th generation, and newer devices.
Chrome only allows one output at a time, so when you start screen sharing, your video call will change to an audio call. When you are finished screen sharing you can turn your video back on.
The bandwidth requirements for using screen sharing in Skype is the same as when you make a video call in Skype. Learn more about how much bandwidth Skype needs.

When making personnel decisions - including hiring, retention, promotion, and reassignment - employers sometimes want to consider the backgrounds of applicants and employees. For example, some employers might try to find out about the person"s work history, education, criminal record, financial history, medical history, or use of social media. Except for certain restrictions related to medical and genetic information (see below), it"s not illegal for an employer to ask questions about an applicant"s or employee"s background, or to require a background check.
However, any time you use an applicant"s or employee"s background information to make an employment decision, regardless of how you got the information, you must comply with federal laws that protect applicants and employees from discrimination. That includes discrimination based on race, color, national origin, sex, or religion; disability; genetic information (including family medical history); and age (40 or older). These laws are enforced by the Equal Employment Opportunity Commission (EEOC).
In addition, when you run background checks through a company in the business of compiling background information, you must comply with the Fair Credit Reporting Act (FCRA). The Federal Trade Commission (FTC) enforces the FCRA. This publication explains how to comply with both the federal nondiscrimination laws and the FCRA. It"s also a good idea to review the laws of your state and municipality regarding background reports or information because some states and municipalities regulate the use of that information for employment purposes.
In all cases, make sure that you"re treating everyone equally. It"s illegal to check the background of applicants and employees when that decision is based on a person"s race, national origin, color, sex, religion, disability, genetic information (including family medical history), or age (40 or older). For example, asking only people of a certain race about their financial histories or criminal records is evidence of discrimination.
Except in rare circumstances, don"t try to get an applicant"s or employee"s genetic information, which includes family medical history. Even if you have that information, don"t use it to make an employment decision. (For more information about this law, see the EEOC"s publications explaining the Genetic Information Nondiscrimination Act, or GINA.) Don"t ask any medical questions before a conditional job offer has been made. If the person has already started the job, don"t ask medical questions unless you have objective evidence that he or she is unable to do the job or poses a safety risk because of a medical condition.
If you get background information (for example, a credit or criminal background report) from a company in the business of compiling background information, there are additional procedures the FCRA requires beforehand:
Tell the applicant or employee you might use the information for decisions about his or her employment. This notice must be in writing and in a stand-alone format. The notice can"t be in an employment application. You can include some minor additional information in the notice (like a brief description of the nature of consumer reports), but only if it doesn"t confuse or detract from the notice.
If you are asking a company to provide an "investigative report" - a report based on personal interviews concerning a person"s character, general reputation, personal characteristics, and lifestyle - you must also tell the applicant or employee of his or her right to a description of the nature and scope of the investigation.
Get the applicant"s or employee"s written permission to do the background check. This can be part of the document you use to notify the person that you will get the report. If you want the authorization to allow you to get background reports throughout the person"s employment, make sure you say so clearly and conspicuously.
Apply the same standards to everyone, regardless of their race, national origin, color, sex, religion, disability, genetic information (including family medical history), or age (40 or older). For example, if you don"t reject applicants of one ethnicity with certain financial histories or criminal records, you can"t reject applicants of other ethnicities because they have the same or similar financial histories or criminal records.
Take special care when basing employment decisions on background problems that may be more common among people of a certain race, color, national origin, sex, or religion; among people who have a disability; or among people age 40 or older. For example, employers should not use a policy or practice that excludes people with certain criminal records if the policy or practice significantly disadvantages individuals of a particular race, national origin, or another protected characteristic, and does not




 Ms.Josey
Ms.Josey 
 Ms.Josey
Ms.Josey