programmable block lcd panel write text made in china
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.

A programmable Logic Controller (PLC) is an industrial process control computer which has been "ruggedized" and adapted to control the manufacturing process. Almost all manufacturing processes are modernized and automated by adapting this technology to stay ahead of competition.
Structured Text is a text based programming language used to design PLC logic and it’s more like python Visual Basic or C. It uses less CPU memory and is good to move a lot of data and complex mathematical calculations. Complex PLC logic is easier to code and understand. Below is a sample:
Some training may be needed to learn this. If you are not familiar with high level programming languages like C, Python or Visual Basic, it’s a little overwhelming for an electrician to learn this and maintain equipment on the fly. Structured Text can be programmer friendly but not Electrician or Maintenance Engineer friendly. You will have to know the Syntax, Expressions, Logical and Bitwise operators and Loops etc.
Conclusion: In many manufacturing plants, electricians take the ownership and maintain the equipment. They are generally not trained to use any programming languages. But they are well versed in ladder logic due to its similarity to hardwired relay logic. You might very well have a million dollar machine, but it is absolutely of no use if the electricians cannot troubleshoot the code written in other languages. Other PLC programming languages may be good for learning in a classroom environment, but not for industrial environment. Minimum downtime is the highest priority in all manufacturing plants. Process or the machine should always stay up and running. A combination of Relay Ladder Logic and Function Blocks is the best way to program a PLC as it is easier for both the programmer and electricians and maintenance personnel.
This website is using a security service to protect itself from online attacks. The action you just performed triggered the security solution. There are several actions that could trigger this block including submitting a certain word or phrase, a SQL command or malformed data.
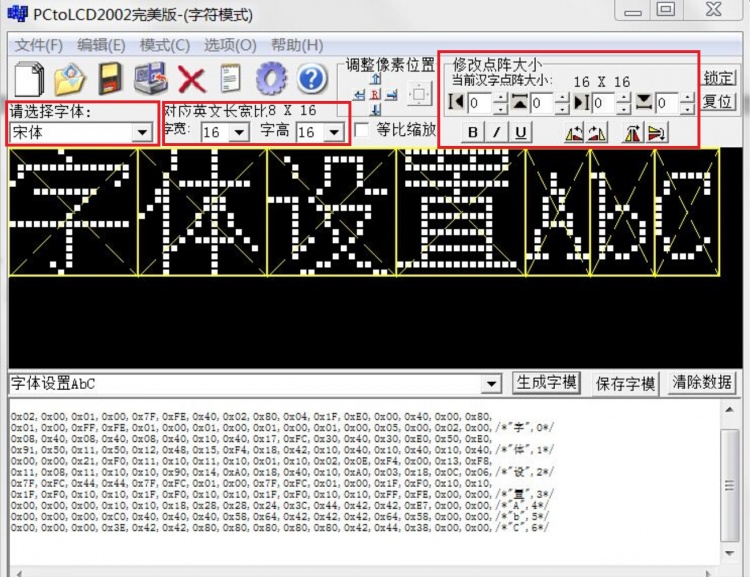
Unicode, formally The Unicode Standard,information technology standard for the consistent encoding, representation, and handling of text expressed in most of the world"s writing systems. The standard, which is maintained by the Unicode Consortium, defines as of the current version (15.0) 149,186 charactersscripts, as well as symbols, emoji (including in colors), and non-visual control and formatting codes.
The Unicode character repertoire is synchronized with ISO/IEC 10646, each being code-for-code identical with the other. The Unicode Standard, however, includes more than just the base code. Alongside the character encodings, the Consortium"s official publication includes a wide variety of details about the scripts and how to display them: normalization rules, decomposition, collation, rendering, and bidirectional text display order for multilingual texts, and so on.Standard also includes reference data files and visual charts to help developers and designers correctly implement the repertoire.
In text processing, Unicode takes the role of providing a unique code point—a number, not a glyph—for each character. In other words, Unicode represents a character in an abstract way and leaves the visual rendering (size, shape, font, or style) to other software, such as a web browser or word processor. This simple aim becomes complicated, however, because of concessions made by Unicode"s designers in the hope of encouraging a more rapid adoption of Unicode.
The first 256 code points were made identical to the content of ISO/IEC 8859-1 so as to make it trivial to convert existing western text. Many essentially identical characters were encoded multiple times at different code points to preserve distinctions used by legacy encodings and therefore, allow conversion from those encodings to Unicode (and back) without losing any information. For example, the "fullwidth forms" section of code points encompasses a full duplicate of the Latin alphabet because Chinese, Japanese, and Korean (CJK) fonts contain two versions of these letters, "fullwidth" matching the width of the CJK characters, and normal width. For other examples, see duplicate characters in Unicode.
Unicode is intended to address the need for a workable, reliable world text encoding. Unicode could be roughly described as "wide-body ASCII" that has been stretched to 16 bits to encompass the characters of all the world"s living languages. In a properly engineered design, 16 bits per character are more than sufficient for this purpose.
Unicode gives higher priority to ensuring utility for the future than to preserving past antiquities. Unicode aims in the first instance at the characters published in modern text (e.g. in the union of all newspapers and magazines printed in the world in 1988), whose number is undoubtedly far below 214 = 16,384. Beyond those modern-use characters, all others may be defined to be obsolete or rare; these are better candidates for private-use registration than for congesting the public list of generally useful Unicodes.
The Unicode Consortium is a nonprofit organization that coordinates Unicode"s development. Full members include most of the main computer software and hardware companies with any interest in text-processing standards, including Adobe, Apple, Facebook, Google, IBM, Microsoft, Netflix, and SAP SE.
As of 2022scriptsalphabets, abugidas and syllabaries), although there are still scripts that are not yet encoded, particularly those mainly used in historical, liturgical, and academic contexts. Further additions of characters to the already encoded scripts, as well as symbols, in particular for mathematics and music (in the form of notes and rhythmic symbols), also occur.
While the UCS is a simple character map, Unicode specifies the rules, algorithms, and properties necessary to achieve interoperability between different platforms and languages. Thus, The Unicode Standard includes more information, covering—in depth—topics such as bitwise encoding, collation and rendering. It also provides a comprehensive catalog of character properties, including those needed for supporting bidirectional text, as well as visual charts and reference data sets to aid implementers. Previously, The Unicode Standard was sold as a print volume containing the complete core specification, standard annexes, and code charts. However, Unicode 5.0, published in 2006, was the last version printed this way. Starting with version 5.2, only the core specification, published as print-on-demand paperback, may be purchased.
The latest version of Unicode, 15.0.0, was released on 13 September 2022. Several annexes were updated including Unicode Security Mechanisms (UTS #39), and a total of 4489 new characters were encoded, including 20 new emoji characters, such as "wireless" (network) symbol and hearts in different colors such as pink, two new scripts, CJK Unified Ideographs extension, and multiple additions to existing blocks.
Chorasmian, Dives Akuru, Khitan small script, Yezidi, 4,969 CJK unified ideographs added (including 4,939 in Ext. G), Arabic script additions used to write Hausa, Wolof, and other languages in Africa and other additions used to write Hindko and Punjabi in Pakistan, Bopomofo additions used for Cantonese, Creative Commons license symbols, graphic characters for compatibility with teletext and home computer systems from the 1970s and 1980s, and 55 emoji.
Toto, Cypro-Minoan, Vithkuqi, Old Uyghur, Tangsa, Latin script additions at SMP blocks (Ext-F, Ext-G) for use in extended IPA, Arabic script additions for use in languages across Africa and in Iran, Pakistan, Malaysia, Indonesia, Java, and Bosnia, and to write honorifics, additions for Quranic use, other additions to support languages in North America, the Philippines, India, and Mongolia, addition of the Kyrgyzstani som currency symbol, support for Znamenny musical notation, and 37 emoji.
A small set of code points are guaranteed never to be used for encoding characters, although applications may make use of these code points internally if they wish. There are sixty-six of these noncharacters: U+FDD0–U+FDEF and any code point ending in the value FFFE or FFFF (i.e., U+FFFE, U+FFFF, U+1FFFE, U+1FFFF, ... U+10FFFE, U+10FFFF). The set of noncharacters is stable, and no new noncharacters will ever be defined.byte order mark (BOM) assumes that U+FFFE will never be the first code point in a text.
Sixty-five code points (U+0000–U+001F and U+007F–U+009F) are reserved as control codes, and correspond to the C0 and C1 control codes defined in ISO/IEC 6429. U+0009 (Tab), U+000A (Line Feed), and U+000D (Carriage Return) are widely used in Unicode-encoded texts. In practice the C1 code points are often improperly-translated (mojibake) as the legacy Windows-1252 characters used by some English and Western European texts.
Unicode includes a mechanism for modifying characters that greatly extends the supported glyph repertoire. This covers the use of combining diacritical marks that may be added after the base character by the user. Multiple combining diacritics may be simultaneously applied to the same character. Unicode also contains precomposed versions of most letter/diacritic combinations in normal use. These make conversion to and from legacy encodings simpler, and allow applications to use Unicode as an internal text format without having to implement combining characters. For example, é can be represented in Unicode as U+0065 (LATIN SMALL LETTER E) followed by U+0301 (COMBINING ACUTE ACCENT), but it can also be represented as the precomposed character U+00E9 (LATIN SMALL LETTER E WITH ACUTE). Thus, in many cases, users have multiple ways of encoding the same character. To deal with this, Unicode provides the mechanism of canonical equivalence.
UTF-8 uses one to four bytes per code point and, being compact for Latin scripts and ASCII-compatible, provides the de facto standard encoding for interchange of Unicode text. It is used by FreeBSD and most recent Linux distributions as a direct replacement for legacy encodings in general text handling.
The UCS-2 and UTF-16 encodings specify the Unicode byte order mark (BOM) for use at the beginnings of text files, which may be used for byte-order detection (or byte endianness detection). The BOM, code point U+FEFF, has the important property of unambiguity on byte reorder, regardless of the Unicode encoding used; U+FFFE (the result of byte-swapping U+FEFF) does not equate to a legal character, and U+FEFF in places other than the beginning of text conveys the zero-width non-break space (a character with no appearance and no effect other than preventing the formation of ligatures).
The same character converted to UTF-8 becomes the byte sequence EF BB BF. The Unicode Standard allows that the BOM "can serve as signature for UTF-8 encoded text where the character set is unmarked".code pages. However RFC 3629, the UTF-8 standard, recommends that byte order marks be forbidden in protocols using UTF-8, but discusses the cases where this may not be possible. In addition, the large restriction on possible patterns in UTF-8 (for instance there cannot be any lone bytes with the high bit set) means that it should be possible to distinguish UTF-8 from other character encodings without relying on the BOM.
In UTF-32 and UCS-4, one 32-bit code unit serves as a fairly direct representation of any character"s code point (although the endianness, which varies across different platforms, affects how the code unit manifests as a byte sequence). In the other encodings, each code point may be represented by a variable number of code units. UTF-32 is widely used as an internal representation of text in programs (as opposed to stored or transmitted text), since every Unix operating system that uses the gcc compilers to generate software uses it as the standard "wide character" encoding. Some programming languages, such as Seed7, use UTF-32 as internal representation for strings and characters. Recent versions of the Python programming language (beginning with 2.2) may also be configured to use UTF-32 as the representation for Unicode strings, effectively disseminating such encoding in high-level coded software.
Unicode has become the dominant scheme for internal processing and storage of text. Although a great deal of text is still stored in legacy encodings, Unicode is used almost exclusively for building new information processing systems. Early adopters tended to use UCS-2 (the fixed-length two-byte obsolete precursor to UTF-16) and later moved to UTF-16 (the variable-length current standard), as this was the least disruptive way to add support for non-BMP characters. The best known such system is Windows NT (and its descendants, 2000, XP, Vista, 7, 8, 10, and 11), which uses UTF-16 as the sole internal character encoding. The Java and .NET bytecode environments, macOS, and KDE also use it for internal representation. Partial support for Unicode can be installed on Windows 9x through the Microsoft Layer for Unicode.
Multilingual text-rendering engines which use Unicode include Uniscribe and DirectWrite for Microsoft Windows, ATSUI and Core Text for macOS, and Pango for GTK+ and the GNOME desktop.
Online tools for finding the code point for a known character include Unicode LookupShape context, one draws the character in a box and a list of characters approximating the drawing, with their code points, is returned.
MIME defines two different mechanisms for encoding non-ASCII characters in email, depending on whether the characters are in email headers (such as the "Subject:"), or in the text body of the message; in both cases, the original character set is identified as well as a transfer encoding. For email transmission of Unicode, the UTF-8 character set and the Base64 or the Quoted-printable transfer encoding are recommended, depending on whether much of the message consists of ASCII characters. The details of the two different mechanisms are specified in the MIME standards and generally are hidden from users of email software.
HTML characters manifest either directly as bytes according to document"s encoding, if the encoding supports them, or users may write them as numeric character references based on the character"s Unicode code point. For example, the references Δ, Й, ק, م, ๗, あ, 叶, 葉, and 말 (or the same numeric values expressed in hexadecimal, with &#x as the prefix) should display on all browsers as Δ, Й, ק ,م, ๗, あ, 叶, 葉, and 말.
Unicode partially addresses the newline problem that occurs when trying to read a text file on different platforms. Unicode defines a large number of characters that conforming applications should recognize as line terminators.
In terms of the newline, Unicode introduced U+2028 LINE SEPARATOR and U+2029 PARAGRAPH SEPARATOR. This was an attempt to provide a Unicode solution to encoding paragraphs and lines semantically, potentially replacing all of the various platform solutions. In doing so, Unicode does provide a way around the historical platform dependent solutions. Nonetheless, few if any Unicode solutions have adopted these Unicode line and paragraph separators as the sole canonical line ending characters. However, a common approach to solving this issue is through newline normalization. This is achieved with the Cocoa text system in Mac OS X and also with W3C XML and HTML recommendations. In this approach every possible newline character is converted internally to a common newline (which one does not really matter since it is an internal operation just for rendering). In other words, the text system can correctly treat the character as a newline, regardless of the input"s actual encoding.
Unicode has been criticized for failing to separately encode older and alternative forms of kanji which, critics argue, complicates the processing of ancient Japanese and uncommon Japanese names. This is often due to the fact that Unicode encodes characters rather than glyphs (the visual representations of the basic character that often vary from one language to another). Unification of glyphs leads to the perception that the languages themselves, not just the basic character representation, are being merged.TRON (although it is not widely adopted in Japan, there are some users who need to handle historical Japanese text and favor it).
Modern font technology provides a means to address the practical issue of needing to depict a unified Han character in terms of a collection of alternative glyph representations, in the form of Unicode variation sequences. For example, the Advanced Typographic tables of OpenType permit one of a number of alternative glyph representations to be selected when performing the character to glyph mapping process. In this case, information can be provided within plain text to designate which alternate character form to select.
If the appropriate glyphs for characters in the same script differ only in the italic, Unicode has generally unified them, as can be seen in the comparison among a set of seven characters" italic glyphs as typically appearing in Russian, traditional Bulgarian, Macedonian and Serbian texts at right, meaning that the differences are displayed through smart font technology or manually changing fonts.
Unicode was designed to provide code-point-by-code-point round-trip format conversion to and from any preexisting character encodings, so that text files in older character sets can be converted to Unicode and then back and get back the same file, without employing context-dependent interpretation. That has meant that inconsistent legacy architectures, such as combining diacritics and precomposed characters, both exist in Unicode, giving more than one method of representing some text. This is most pronounced in the three different encoding forms for Korean Hangul. Since version 3.0, any precomposed characters that can be represented by a combining sequence of already existing characters can no longer be added to the standard in order to preserve interoperability between software using different versions of Unicode.
Indic scripts such as Tamil and Devanagari are each allocated only 128 code points, matching the ISCII standard. The correct rendering of Unicode Indic text requires transforming the stored logical order characters into visual order and the forming of ligatures (aka conjuncts) out of components. Some local scholars argued in favor of assignments of Unicode code points to these ligatures, going against the practice for other writing systems, though Unicode contains some Arabic and other ligatures for backward compatibility purposes only.Tibetan script in 2003 when the Standardization Administration of China proposed encoding 956 precomposed Tibetan syllables,ISO/IEC JTC 1/SC 2).
Internet censorship in the People"s Republic of China (PRC) affects both publishing and viewing online material. Many controversial events are censored from news coverage, preventing many Chinese citizens from knowing about the actions of their government, and severely restricting freedom of the press.Great Firewall of China",blocks websites. Methods used to block websites and pages include DNS spoofing, blocking access to IP addresses, analyzing and filtering URLs, packet inspection, and resetting connections.
Commonly alleged user offenses include communicating with organized groups abroad, signing controversial online petitions, and forcibly calling for government reform. The government has escalated its efforts to reduce coverage and commentary that is critical of the regime after a series of large anti-pollution and anti-corruption protests. Many of these protests were organized or publicized using instant messaging services, chat rooms, and text messages.Internet police force was reported by official state media to be 2 million strong in 2013.
In December 1997, The Public Security Minister, Zhu Entao, released new regulations to be enforced by the ministry that inflicted fines for "defaming government agencies, splitting the nation, and leaking state secrets." Violators could face a fine of up to CNY 15,000 (roughly US$1,800).websites allowed in one city, yet similar sites blocked in another. The blocks were often lifted for special occasions. For example, CCP General Secretary Jiang Zemin specifically asked about the block and he replied that he would look into the matter. During the APEC summit in Shanghai during 2001, normally-blocked media sources such as CNN, NBC, and the mainland China. However, access to the New York Times was denied again in December 2008.
In the middle of 2005, China purchased over 200 routers from an American company, Cisco Systems, which enabled the Chinese government to use more advanced censor technology.Google, in exchange for equipment installation on Chinese soil, blocked websites which the Chinese government deemed illegal.backdoors into their software.
In July 2019, the CAC announced a regulation that said that Internet information providers and users in China who seriously violate related laws and regulations will be subject to Social Credit System blocklist. It also announces that Internet information providers and users who are not meeting the standard but mildly violation will be recorded in the List to Focus.
On 11 July 2003, the Chinese government started granting licenses to businesses to open Internet cafe chains. Business analysts and foreign Internet operators regard the licenses as intended to clamp down on information deemed harmful to the Chinese government. In July 2007, the city of Xiamen announced it would ban anonymous online postings after text messages and online communications were used to rally protests against a proposed chemical plant in the city. Internet users will be required to provide proof of identity when posting messages on the more than 100,000 Web sites registered in Xiamen.
The Great Firewall has used numerous methods to block content, including IP dropping, DNS spoofing, deep packet inspection for finding plain text signatures within the handshake to throttle protocols,
According to a Harvard study, at least 18,000 websites were blocked from within mainland China in 2002,Gmail is blocked, and it cannot be said to fall into any of these categories.Falun Gong,police brutality, the 1989 Tiananmen Square protests and massacre, freedom of speech, democracy,Tibetan independence movement,Tuidang movement.The New York Times, the BBC, and Bloomberg News are blocked indefinitely.
A 2012 study of social media sites by other Harvard researchers found that 13% of Internet posts were blocked. The blocking focused mainly on any form of collective action (anything from false rumors driving riots to protest organizers to large parties for fun), pornography, and criticism of the censors. However, significant criticisms of the government were not blocked when made separately from calls for collective action. Another study has shown comments on social media that criticize the state, its leaders, and their policies are usually published, but posts with collective action potential will be more likely to be censored whether they are against the state or not.
A lot of larger Japanese websites were blocked from the afternoon of 15 June 2012 (UTC+08:00) to the morning of 17 June 2012 (UTC+08:00), such as Google Japan, Yahoo! Japan, Amazon Japan, Excite, Yomiuri News, Sponichi News and Nikkei BP Japan.
Chinese censors have been relatively reluctant to block websites where there might be significant economic consequences. For example, a block of GitHub was reversed after widespread complaints from the Chinese software developer community.Reuters and the greatfire.org mirrored the Reuters website to an Amazon.com domain in such a way that it could not be shut down without shutting off domestic access to all of Amazon"s cloud storage service.
For one month beginning 17 November 2014, ProPublica tested whether the homepages of 18 international news organizations were accessible to browsers inside China, and found the most consistently blocked were Bloomberg, New York Times, South China Morning Post, Wall Street Journal, Facebook, and Twitter.
One part of the block is to filter the search results of certain terms on Chinese search engines such as (for example, Sogou, 360 Search and Baidu). Attempting to search for censored keywords in these Chinese search engines will yield few or no results.
In addition, a connection containing intensive censored terms may also be closed by The Great Firewall, and cannot be re-established for several minutes. This affects all network connections including HTTP and POP, but the reset is more likely to occur during searching. Before the search engines censored themselves, many search engines had been blocked.
In September 2007, some data centers were shut down indiscriminately for providing interactive features such as blogs and forums. CBS reports an estimate that half the interactive sites hosted in China were blocked.
In the second half of 2009, the social networking sites Facebook and Twitter were blocked, presumably because of containing social or political commentary (similar to LiveJournal in the above list). An example is the commentary on the July 2009 Ürümqi riots.
WeChat is the dominant social media and messaging app in China, and is also the most popular messaging application for most Chinese nationals staying overseas. Though subject to state rules which saw individual posts removed,Tech in Asia reported in 2013 that certain "restricted words" had been blocked on WeChat globally.CNN reported that the blocks were related to laws banning the spread of political "rumors".
In March 2020, China suddenly started blocking website using the TLS (Transport Layer Security 1.3) and ESNI (Encrypted Server Name Indicator) for SSL certificates, since ESNI makes it difficult if not impossible to identify the name of a website based on the server name displayed in its SSL certificate.Chinese Wikipedia has been blocked in mainland China.HTTPS encryption, which made selective censorship more difficult.
Beginning in 2018, the Ministry of Industry and Information Technology (MIIT) in conjunction with the Cyberspace Administration Commission (CAC) began a sweeping crackdown on all VPN providers, ordering all major state owned telecommunications providers including China Telecom, China Mobile and China Unicom to block VPN protocols with only authorised users who have obtained permits beforehand to access VPN"s (provided they are operated by state-owned telecommunications companies).Apple also started removing all VPN apps from Apple app stores at the behest of the Chinese government.
In 2009, the Guardian wrote that Chinese netizens responded with subtle protests against the government"s temporary blockages of large web services. For instance, Chinese websites made subtle grievances against the state"s censorship by sarcastically calling the date 4 June as the 中国互联网维护日[zh] or "Chinese Internet Maintenance Day".rubber ducks sculptures replacing tanks in the Tank Man photo.
Foreign content providers such as Yahoo!, AOL, and Skype must abide by Chinese government wishes, including having internal content monitors, to be able to operate within mainland China. Also, per mainland Chinese laws, Microsoft began to censor the content of its blog service Windows Live Spaces, arguing that continuing to provide Internet services is more beneficial to the Chinese.Michael Anti"s blog on Windows Live Spaces was censored by Microsoft. In an April 2006 e-mail panel discussion Rebecca MacKinnon, who reported from China for nine years as a Beijing bureau chief for CNN, said: "... many bloggers said he [Anti] was a necessary sacrifice so that the majority of Chinese can continue to have an online space to express themselves as they choose. So the point is, compromises are being made at every level of society because nobody expects political freedom anyway."
Internet censorship in China is circumvented by determined parties by using proxy servers outside the firewall.VPN or SSH connection method to a computer outside mainland China. However, disruptions of VPN services have been reported and the free or popular services especially are increasingly being blocked.2022 COVID-19 protests in China, the Chinese government intensified crackdowns on VPNs.deep packet inspection and continue providing services in China some VPN providers implemented server obfuscation.
Although many users use VPNs to circumvent the Great Firewall of China, many Internet connections are now subject to deep packet inspection, in which data packets are looked at in detail. Many VPNs have been blocked using this method. Blogger Grey One suggests users trying to disguise VPN usage forward their VPN traffic through port 443 because this port is also heavily used by web browsers for HTTPS connections. However, Grey points out this method is futile against advanced inspection.
The Tor anonymity network was and is subject to partial blocking by China"s Great Firewall.HTTP but it is reachable over HTTPS so it is possible for users to download the Tor Browser Bundle.
It was common in the past to use Google"s cache feature to view blocked websites. However, this feature of Google seems to be under some level of blocking, as access is now erratic and does not work for blocked websites. Currently, the block is mostly circumvented by using proxy servers outside the firewall and is not difficult to carry out for those determined to do so.
According to steganography, a practice of "embedding useful data in what looks like something irrelevant. The text of a document can be broken into its constituent bytes, which are added to the pixels of an innocent picture. The effect is barely visible on the picture, but the recipient can extract it with the right software".
According to the BBC, local Chinese businesses such as Baidu, Tencent and Alibaba, some of the world"s largest Internet enterprises, benefited from the way China has blocked international rivals from the market, encouraging domestic competition.
Bradsher, Keith (20 December 2008). "China Blocks Access to The Times"s Web Site". The New York Times. Archived from the original on 2 May 2013. Retrieved 31 March 2010.
"UNPRECEDENTED: China Blocked Every Japanese Domain For Almost Two Days Last Week". Business Insider Australia. 19 June 2012. Archived from the original on 12 July 2020. Retrieved 10 May 2017.
Skipper, Ben (7 December 2015). "China"s government has blocked Wikipedia in its entirety again". International Business Times UK. Archived from the original on 3 May 2018. Retrieved 2 May 2018.
"Chinese Wikipedia Blocked by Great Firewall". China Digital Times (CDT). 20 May 2015. Archived from the original on 4 May 2017. Retrieved 4 May 2017.
Stanway, David; Qiu, Stella (21 June 2018). "China"s Weibo blocks comedian John Oliver after Xi Jinping roasting". Reuters. Archived from the original on 21 June 2018. Retrieved 21 June 2018.
28c3: How governments have tried to block Tor. 28c3. 29 December 2011. Archived from the original on 15 July 2022. Retrieved 2 December 2022 – via YouTube.

With piped text, you can customize question and answer choice wording for each respondent, allowing each of them to have a customized, dynamic, and personal survey experience. Piped text is a line of code you add to your survey that pulls information from different sources and displays that information to the respondent (or can be used in display logic, embedded data, and other areas).
Example: After asking about a respondent’s preferred product, you can pull their selected answer into a follow up question and have it displayed in the question text.
Though piped text appears as a line of code in your survey editor, when respondents take the survey, this code will be replaced with the specified content.
Qtip: Want to watch a video on how to use piped text? Visit Configuring Your Project on XM Basecamp for a guided learning experience. Access is included as part of your Qualtrics account.
Qtip: If you’d like to use piped text in an area that does not have the piped text menu, simply generate the piped text in one of the above areas and then copy and paste the code into the desired location. For example, while you may need to set custom validation equal to a piped text value, you will need to generate this piped text in another location.
Qtip: Using the rich content editor, you can style the piped text code with all the options available for regular text, such as bolding and italicizing.
Attention: A question must be submitted by the respondent using the next button before piped text will work. If you pipe in the selected answer from one question to another, there must be a page breakin between the two questions for the Piped Text to load.
Qtip: When inserted into your survey, the piped text will be in the general format: ${q://QIDX/SelectedValue}. The field “QIDX” is the internal question ID for the selected question and should not be edited. Editing the question ID will cause the piped text to stop working.
Description: Refers to previous answer choice text. For example, if they select “Less than 1 month – Description,” the piped text would bring in “Less than 1 month.”
Text Entry: Pipes any text a respondent enters. For example, if your respondent picks “Other” and types in “Three Years,” the “Other (Text Entry)” piped text would bring forward “Three Years.”
Qtip: There is one more option that is not in the piped text menu called Selected Choices Count, which shows the number of choices the respondent selected in a question where they can pick multiple answers. The format for the selected count piped text is ${q://QIDX/SelectedChoicesCount}. For example, if you want to show the number of selected answers for Q12, it’d be ${q://QID12/SelectedChoicesCount}. If Q12 is a matrix table and you want selected count for the second statement, the piped text is ${q://QID12/SelectedChoicesCount/2}. Since QID can differ from the question’s number (e.g., Q12), be careful to generate another line of piped text for that question to double-check the QID.
Earlier, we mentioned that when you pipe text from a previous question into a following question, you need to be careful of the order content appears, and of page breaks. These same rules apply when working with embedded data.
When putting your embedded data element in the survey flow, think carefully about the order of elements. If your embedded data is not reliant on the respondent answering questions to determine a value, it’s generally best practice to make sure the embedded data is at the top of the survey flow, so it is saved before the respondent reaches any piped text you have displayed.
If the embedded data is reliant on the respondent answering certain questions before it can generate a value (as with math operations), then those questions need to appear in a block before the embedded data is set in the survey flow, and the questions where the embedded data is piped in and displayed to respondents must appear after the embedded data element. You may need to move questions to new blocks to achieve this.
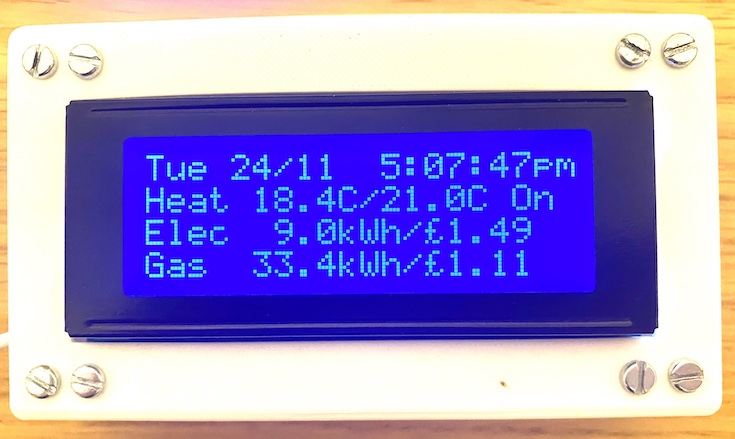
Through the date / time piped text, you can display the current date and time in your survey, as well as other dates. This is useful to display in event registration surveys as a time reference for your respondents.
The timezone of date / time piped text is based off the timezone set in your account when the response was submitted. If you adjust the timezone in your account after responses are submitted, the data collected will not change.
Qtip: You may use the Other Date piped text to display any date in relation to the current date. For example, if you choose to display tomorrow’s date, the piped text will look like ${date://OtherDate/PT/+1%20day}. If you change the number before the percent sign, you can choose to display any date. Changing the piped text to ${date://OtherDate/PT/+50%20day} will show the date 50 days after today. This also works with “negative” days. ${date://OtherDate/PT/-10%20day} will show the date ten days before today. If you want to change the time zone in your piped text, you can use ${date://OtherDate/G:i/+1%20hours} as a model. The “+1” will make the time 1 time zone later. The same thing can be done using a minus sign to display an earlier time.
You can change the language date / time piped text is recorded in. At the end of the piped text, but inside the last bracket, include a question mark ( ? ), the word locale, and set it equal to a language code of your choosing.
If you are sending your survey to a contact list (also sometimes known as a panel), you can pipe information from that contact list into your survey or email invitation. These fields include basic information like first name, last name, and email, as well as the specialty fields External Data Reference and Language.
With loop & merge, you can repeat a series of questions for a respondent that asks about a different item each time. Piped text is critical for loop & merge so that the respondent knows which item they are responding about.
With quotas, you can make sure that you only gather the right amount of data required for your study. Using piped text, you can display three pieces of information about your quota:
Piped text can be used to generate and display a random number to each of your respondents. When in the survey editor, it will appear as a line of code just like all other piped text. The algorithm that Qualtrics uses for randomization is called the Mersenne Twister.

Internet censorship in the People"s Republic of China (PRC) affects both publishing and viewing online material. Many controversial events are censored from news coverage, preventing many Chinese citizens from knowing about the actions of their government, and severely restricting freedom of the press.Great Firewall of China",blocks websites. Methods used to block websites and pages include DNS spoofing, blocking access to IP addresses, analyzing and filtering URLs, packet inspection, and resetting connections.
Commonly alleged user offenses include communicating with organized groups abroad, signing controversial online petitions, and forcibly calling for government reform. The government has escalated its efforts to reduce coverage and commentary that is critical of the regime after a series of large anti-pollution and anti-corruption protests. Many of these protests were organized or publicized using instant messaging services, chat rooms, and text messages.Internet police force was reported by official state media to be 2 million strong in 2013.
In December 1997, The Public Security Minister, Zhu Entao, released new regulations to be enforced by the ministry that inflicted fines for "defaming government agencies, splitting the nation, and leaking state secrets." Violators could face a fine of up to CNY 15,000 (roughly US$1,800).websites allowed in one city, yet similar sites blocked in another. The blocks were often lifted for special occasions. For example, CCP General Secretary Jiang Zemin specifically asked about the block and he replied that he would look into the matter. During the APEC summit in Shanghai during 2001, normally-blocked media sources such as CNN, NBC, and the mainland China. However, access to the New York Times was denied again in December 2008.
In the middle of 2005, China purchased over 200 routers from an American company, Cisco Systems, which enabled the Chinese government to use more advanced censor technology.Google, in exchange for equipment installation on Chinese soil, blocked websites which the Chinese government deemed illegal.backdoors into their software.
In July 2019, the CAC announced a regulation that said that Internet information providers and users in China who seriously violate related laws and regulations will be subject to Social Credit System blocklist. It also announces that Internet information providers and users who are not meeting the standard but mildly violation will be recorded in the List to Focus.
On 11 July 2003, the Chinese government started granting licenses to businesses to open Internet cafe chains. Business analysts and foreign Internet operators regard the licenses as intended to clamp down on information deemed harmful to the Chinese government. In July 2007, the city of Xiamen announced it would ban anonymous online postings after text messages and online communications were used to rally protests against a proposed chemical plant in the city. Internet users will be required to provide proof of identity when posting messages on the more than 100,000 Web sites registered in Xiamen.
The Great Firewall has used numerous methods to block content, including IP dropping, DNS spoofing, deep packet inspection for finding plain text signatures within the handshake to throttle protocols,
According to a Harvard study, at least 18,000 websites were blocked from within mainland China in 2002,Gmail is blocked, and it cannot be said to fall into any of these categories.Falun Gong,police brutality, the 1989 Tiananmen Square protests and massacre, freedom of speech, democracy,Tibetan independence movement,Tuidang movement.The New York Times, the BBC, and Bloomberg News are blocked indefinitely.
A 2012 study of social media sites by other Harvard researchers found that 13% of Internet posts were blocked. The blocking focused mainly on any form of collective action (anything from false rumors driving riots to protest organizers to large parties for fun), pornography, and criticism of the censors. However, significant criticisms of the government were not blocked when made separately from calls for collective action. Another study has shown comments on social media that criticize the state, its leaders, and their policies are usually published, but posts with collective action potential will be more likely to be censored whether they are against the state or not.
A lot of larger Japanese websites were blocked from the afternoon of 15 June 2012 (UTC+08:00) to the morning of 17 June 2012 (UTC+08:00), such as Google Japan, Yahoo! Japan, Amazon Japan, Excite, Yomiuri News, Sponichi News and Nikkei BP Japan.
Chinese censors have been relatively reluctant to block websites where there might be significant economic consequences. For example, a block of GitHub was reversed after widespread complaints from the Chinese software developer community.Reuters and the greatfire.org mirrored the Reuters website to an Amazon.com domain in such a way that it could not be shut down without shutting off domestic access to all of Amazon"s cloud storage service.
For one month beginning 17 November 2014, ProPublica tested whether the homepages of 18 international news organizations were accessible to browsers inside China, and found the most consistently blocked were Bloomberg, New York Times, South China Morning Post, Wall Street Journal, Facebook, and Twitter.
One part of the block is to filter the search results of certain terms on Chinese search engines such as (for example, Sogou, 360 Search and Baidu). Attempting to search for censored keywords in these Chinese search engines will yield few or no results.
In addition, a connection containing intensive censored terms may also be closed by The Great Firewall, and cannot be re-established for several minutes. This affects all network connections including HTTP and POP, but the reset is more likely to occur during searching. Before the search engines censored themselves, many search engines had been blocked.
In September 2007, some data centers were shut down indiscriminately for providing interactive features such as blogs and forums. CBS reports an estimate that half the interactive sites hosted in China were blocked.
In the second half of 2009, the social networking sites Facebook and Twitter were blocked, presumably because of containing social or political commentary (similar to LiveJournal in the above list). An example is the commentary on the July 2009 Ürümqi riots.
WeChat is the dominant social media and messaging app in China, and is also the most popular messaging application for most Chinese nationals staying overseas. Though subject to state rules which saw individual posts removed,Tech in Asia reported in 2013 that certain "restricted words" had been blocked on WeChat globally.CNN reported that the blocks were related to laws banning the spread of political "rumors".
In March 2020, China suddenly started blocking website using the TLS (Transport Layer Security 1.3) and ESNI (Encrypted Server Name Indicator) for SSL certificates, since ESNI makes it difficult if not impossible to identify the name of a website based on the server name displayed in its SSL certificate.Chinese Wikipedia has been blocked in mainland China.HTTPS encryption, which made selective censorship more difficult.
Beginning in 2018, the Ministry of Industry and Information Technology (MIIT) in conjunction with the Cyberspace Administration Commission (CAC) began a sweeping crackdown on all VPN providers, ordering all major state owned telecommunications providers including China Telecom, China Mobile and China Unicom to block VPN protocols with only authorised users who have obtained permits beforehand to access VPN"s (provided they are operated by state-owned telecommunications companies).Apple also started removing all VPN apps from Apple app stores at the behest of the Chinese government.
In 2009, the Guardian wrote that Chinese netizens responded with subtle protests against the government"s temporary blockages of large web services. For instance, Chinese websites made subtle grievances against the state"s censorship by sarcastically calling the date 4 June as the 中国互联网维护日[zh] or "Chinese Internet Maintenance Day".rubber ducks sculptures replacing tanks in the Tank Man photo.
Foreign content providers such as Yahoo!, AOL, and Skype must abide by Chinese government wishes, including having internal content monitors, to be able to operate within mainland China. Also, per mainland Chinese laws, Microsoft began to censor the content of its blog service Windows Live Spaces, arguing that continuing to provide Internet services is more beneficial to the Chinese.Michael Anti"s blog on Windows Live Spaces was censored by Microsoft. In an April 2006 e-mail panel discussion Rebecca MacKinnon, who reported from China for nine years as a Beijing bureau chief for CNN, said: "... many bloggers said he [Anti] was a necessary sacrifice so that the majority of Chinese can continue to have an online space to express themselves as they choose. So the point is, compromises are being made at every level of society because nobody expects political freedom anyway."
Internet censorship in China is circumvented by determined parties by using proxy servers outside the firewall.VPN or SSH connection method to a computer outside mainland China. However, disruptions of VPN services have been reported and the free or popular services especially are increasingly being blocked.2022 COVID-19 protests in China, the Chinese government intensified crackdowns on VPNs.deep packet inspection and continue providing services in China some VPN providers implemented server obfuscation.
Although many users use VPNs to circumvent the Great Firewall of China, many Internet connections are now subject to deep packet inspection, in which data packets are looked at in detail. Many VPNs have been blocked using this method. Blogger Grey One suggests users trying to disguise VPN usage forward their VPN traffic through port 443 because this port is also heavily used by web browsers for HTTPS connections. However, Grey points out this method is futile against advanced inspection.
The Tor anonymity network was and is subject to partial blocking by China"s Great Firewall.HTTP but it is reachable over HTTPS so it is possible for users to download the Tor Browser Bundle.
It was common in the past to use Google"s cache feature to view blocked websites. However, this feature of Google seems to be under some level of blocking, as access is now erratic and does not work for blocked websites. Currently, the block is mostly circumvented by using proxy servers outside the firewall and is not difficult to carry out for those determined to do so.
According to steganography, a practice of "embedding useful data in what looks like something irrelevant. The text of a document can be broken into its constituent bytes, which are added to the pixels of an innocent picture. The effect is barely visible on the picture, but the recipient can extract it with the right software".
According to the BBC, local Chinese businesses such as Baidu, Tencent and Alibaba, some of the world"s largest Internet enterprises, benefited from the way China has blocked international rivals from the market, encouraging domestic competition.
Bradsher, Keith (20 December 2008). "China Blocks Access to The Times"s Web Site". The New York Times. Archived from the original on 2 May 2013. Retrieved 31 March 2010.
"UNPRECEDENTED: China Blocked Every Japanese Domain For Almost Two Days Last Week". Business Insider Australia. 19 June 2012. Archived from the original on 12 July 2020. Retrieved 10 May 2017.
Skipper, Ben (7 December 2015). "China"s government has blocked Wikipedia in its entirety again". International Business Times UK. Archived from the original on 3 May 2018. Retrieved 2 May 2018.
"Chinese Wikipedia Blocked by Great Firewall". China Digital Times (CDT). 20 May 2015. Archived from the original on 4 May 2017. Retrieved 4 May 2017.
Stanway, David; Qiu, Stella (21 June 2018). "China"s Weibo blocks comedian John Oliver after Xi Jinping roasting". Reuters. Archived from the original on 21 June 2018. Retrieved 21 June 2018.
28c3: How governments have tried to block Tor. 28c3. 29 December 2011. Archived from the original on 15 July 2022. Retrieved 2 December 2022 – via YouTube.
To set a different font for your text, you use the font-family property — this allows you to specify a font (or list of fonts) for the browser to apply to the selected elements. The browser will only apply a font if it is available on the machine the website is being accessed on; if not, it will just use a browser default font. A simple example looks like so:
Most of the time, as web developers we want to have more specific control over the fonts used to display our text content. The problem is to find a way to know which font is available on the computer used to see our web pages. There is no way to know this in every case, but the web safe fonts are known to be available on nearly all instances of the most used operating systems (Windows, macOS, the most common Linux distributions, Android, and iOS).

A few weeks ago, I wrote this article about using a text variable as an array, either an array of strings or an array of numbers, using the covx conversion function in addition for the latter, to extract single elements with the help of the spstr function. It"s a convenient and almost a "one fits all" solution for most use cases and many of the demo projects or the sample code attached to the Nextion Sunday Blog articles made use of it, sometimes even without mentioning it explicitly since it"s almost self-explaining. Then, I got a message from a reader, writing: "... Why then didn"t you use it for the combined sine / cosine lookup table in the flicker free turbo gauge project?"105 editions of the Nextion Sunday blog in a little over two years - time to look back and forth at the same time. Was all the stuff I wrote about interesting for my readers? Is it possible at all to satisfy everybody - hobbyists, makers, and professionals - at the same time? Are people (re-)using the many many HMI demo projects and code snippets? Is anybody interested in the explanation of all the underlying basics like the algorithms for calculating square roots and trigonometric functions with Nextion"s purely integer based language? Are optimized code snippets which allow to save a few milliseconds here and there helpful to other developers?Looking through the different Nextion user groups on social networks, the Nextion user forum and a few not so official but Nextion related forums can be surprising. Sometimes, Nextion newbies ask questions or have issues although the required function is well (in a condensed manner for the experienced developer, I admit) documented on the Nextion Instruction Set page, accessible through the menu of this website. On top of that, there is for sure one of my more than 100 Sunday blog articles which deals not only with that function, but goes often even beyond the usual usage of it. Apparently, I should sometimes move away from always trying to push the limits and listen to the "back to the roots!" calls by my potential readers...Do you remember the (almost) full screen sized flicker free and ultra rapid gauge we designed in June? And this without using the built-in Gauge component? If not, it"s time to read this article first, to understand today"s improvements. The June 2022 version does its job perfectly, the needle movement is quick and smooth, and other components can be added close to the outer circle without flickering since there is no background which needs constantly to be redrawn. But there was a minor and only esthetic weak point: The needle was a 1px thin line, sometimes difficult to see. Thus, already a short time after publishing, some readers contacted me and asked if there were a way to make the needle thicker, at least 2 pixels.Recently, when playing with a ESP32 based NodeMCU 32S and especially with its WiFi configuration, I did as (I guess) everybody does: I loaded an example sketch to learn more about the Wifi library. When you set up the ESP32 as an access point, creating its own wireless network, everything is pretty straightforward. You can easily hard code the Wifi name (SSID) and the password. But what about the client mode ? Perhaps one needs to use it in different environments. And then, a hard coded network name and password are definitively not the best solution. Thus, I thought, why not use a Nextion HMI for a dynamic WiFi setup functionality?Although the Nextion MIDI I/O interface has been primarily designed as an add-on for Nextion HMI screens to transform these in fully autonomous MIDI devices as shown in previous blog posts here, it is also of great use for any Arduino based electronic music project! Many MIDI projects for Arduino suffer from a lack good hardware support. There are sophisticated code, excellent libraries and an infinity of use cases, but afterwards, things tend not to work in a rather rough environment in the studio or on stage. That"s because two resistors and a few Dupont wires on a breadboard besides the Arduino are not really an interface which could drive your Synth, Sequencer, or Drum machine over a 5m long MIDI cable.




 Ms.Josey
Ms.Josey 
 Ms.Josey
Ms.Josey